| Difficulty | Beginner |
|---|---|
| Points | 20 |
| Category | Networking |
Description
 Com veureu, sembla que el grup d'atacants es diu Oblivion, però de l'executable no sabem res sobre què fa, ni per a què serveix...
Comenceu la vostra investigació i descobriu el que pugueu. El que ens interessa és on es connecta, si és que ho fa.
Aleshores, el token del joc serà l'adreça IP de destinació...
Com veureu, sembla que el grup d'atacants es diu Oblivion, però de l'executable no sabem res sobre què fa, ni per a què serveix...
Comenceu la vostra investigació i descobriu el que pugueu. El que ens interessa és on es connecta, si és que ho fa.
Aleshores, el token del joc serà l'adreça IP de destinació...🇺🇸 As you can see, it looks like the group of attackers is named Oblivion, but we know nothing about the executable file nor what it does... Start investigating and discover as much as you can. The crucial part is finding where it connects (If it does...) The flag for this challenge will be the target IP of the program.
Solution walkthrough
We’re presented with a downloadable file named ‘malware’ (How appropiate); we download it and we start by doing all the low-hanging-fruit stuff.
$ file malware
malware: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2,
BuildID[sha1]=ac40f3d3f795f9ee657f59a09fbedea23c4d7e25, for GNU/Linux 2.6.32, strippedThe usual stuff, note that it’s stripped so if we have to debug it; it’ll be harder.
You can run strings but we warned that it’s a 12.3MB file so it’ll take quite an amount of space of your terminal.
If you run it, you’ll probably find out that it’s a Python-packaged ELF file.
My instinct kicked in and I started to search for Python decompilers.
That was an error, the solution is far more easier than that; anyways, I decompiled the ELF file and found out that the .pyc files were Python 3.9 Bytecode which can’t be disassembled as of right now (10/07/2022) so I had to abandon that path.
I’m not sure that compiling it w/3.9 was made on pruppose (To make us not able to decompile it) but there goes that.
Anyways, I proceeded to run the program:
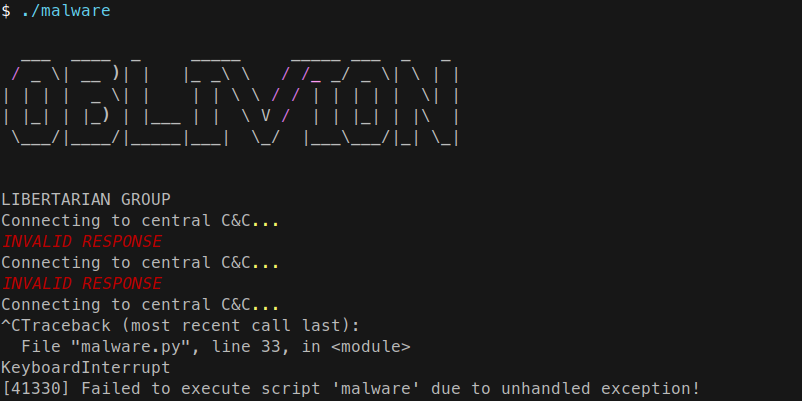
Interesting… I tried ltrace but as soon as Python code is executed, it doesn’t output anything meaningless so I followed another path.
The netstat command helps us identify the network connections, routing tables, interface statistics and more at the time of execution, let’s use it and filter by ‘malware’ which is the name of the binary.
$ netstat --tcp -np | grep "malware"
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 192.168.1.136:54604 45.33.32.156:9929 ESTABLISHED 45512/./malwareFlag: 45.33.32.156